Singularity Threat Intelligence provides a deeper understanding of your threat landscape, monitoring emerging threats to proactively reduce risk and identify adversaries in your environment.
Actionable Intelligence to Protect Your Organization From Adversaries
Enhance Threat Detection, Investigation and Incident Response
with Industry Leading Threat Intelligence
Adversary Intelligence Powered by Mandiant
Singularity Threat Intelligence is powered by Mandiant (now a part of Google Cloud), who is widely recognized as a leader in threat intelligence. Mandiant intelligence is curated by:
- 500 threat intelligence experts across 30 countries speaking over 30 languages
- Insights from over 1,800 breach responses annually
- 200,000 hours of incident response per year
- Frontline intelligence from Mandiant IR & MDR services
- Both open-source threat intelligence (OSINT) and proprietary intelligence


Triage Security Alerts with Adversary Context
Context is key when it comes to effective security alert triage and incident response. Singularity Threat Intelligence contextualizes incidents so you can understand the broader threat landscape to more efficiently and effectively investigate a threat.
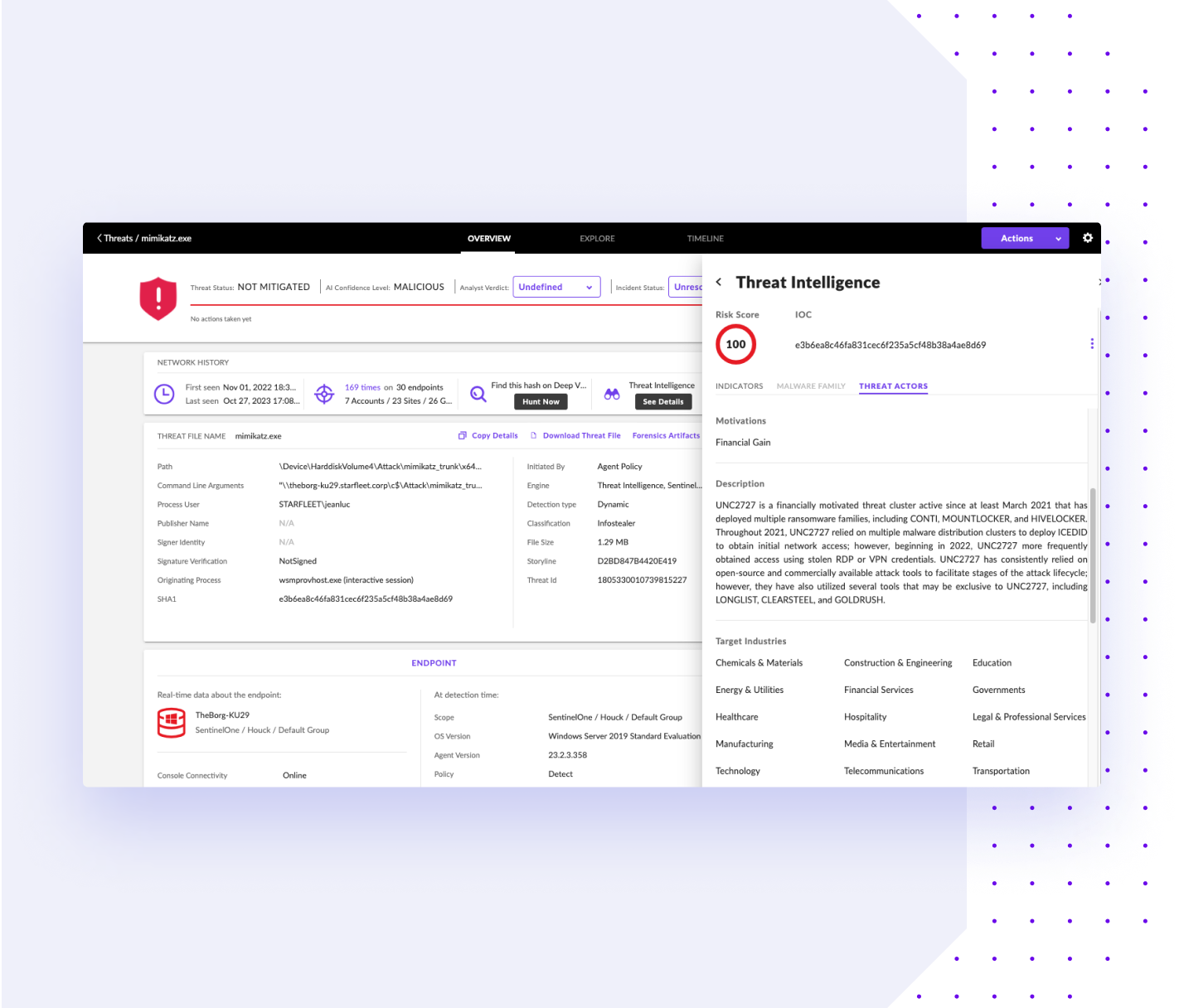

Identify Threat Actors with High-Fidelity Detections
Prioritize incident investigations like never before, empowering you to focus on high-priority threats in your environment. Use auto-response policies when Indicators of Compromise (IOCs) are identified, ensuring swift action is taken to neutralize potential risks.
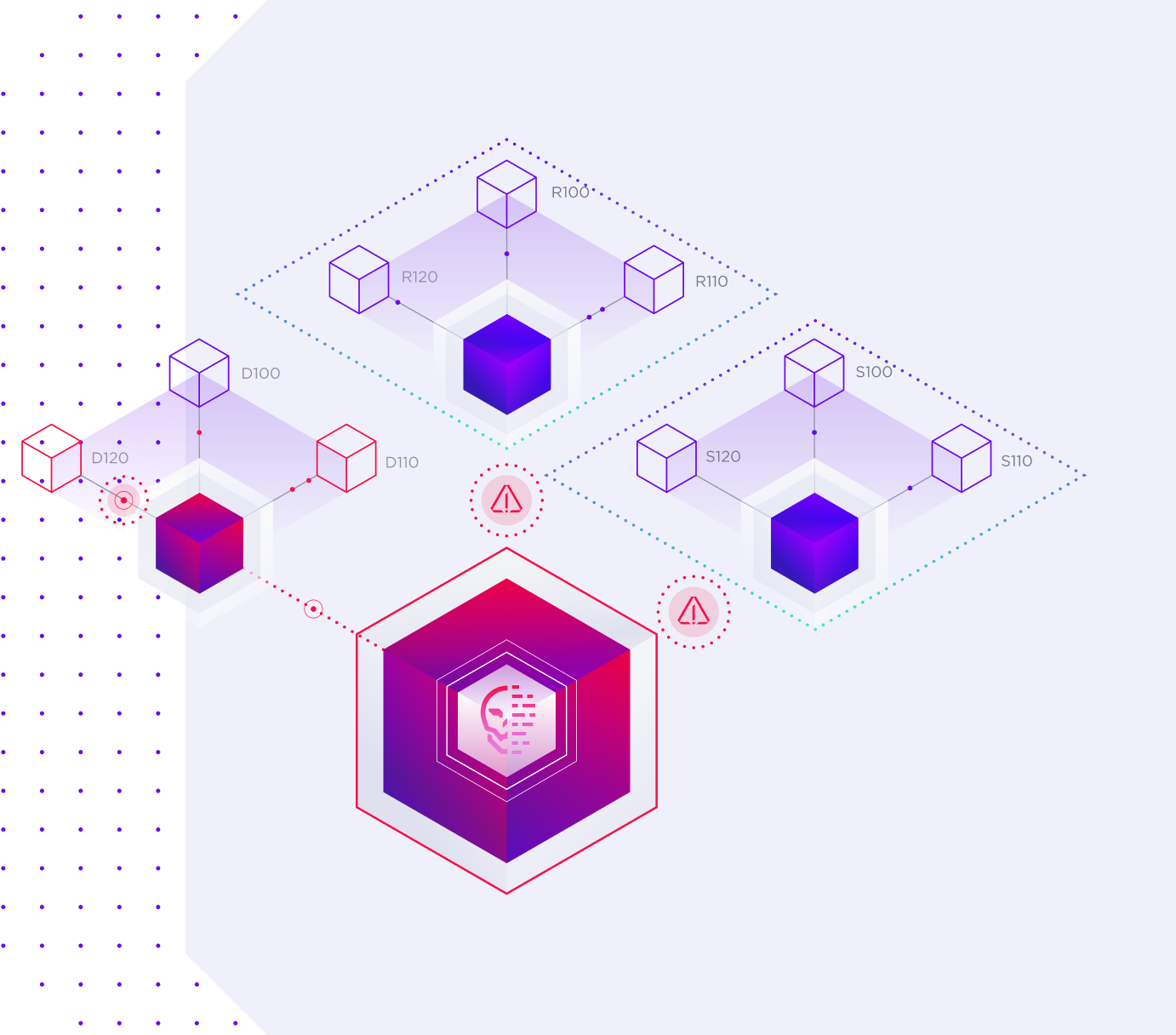

Intelligence-Led Threat Hunting
Singularity Threat Intelligence highlights IOCs found within your network, providing you with valuable leads to initiate targeted threat hunting activities. Built on Singularity Data Lake, you can proactively hunt for threats across security tools and preemptively neutralize them before they cause harm.

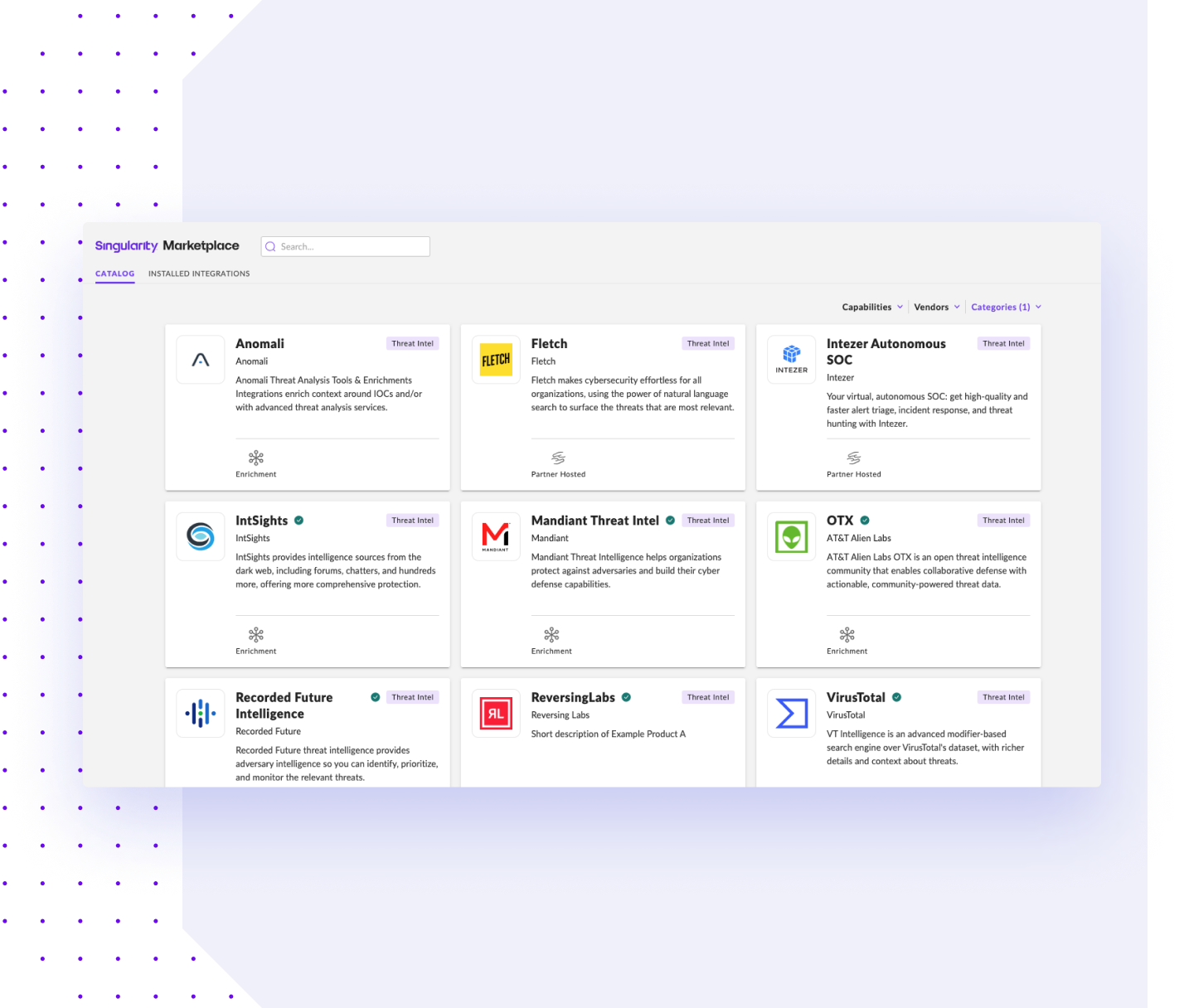
Integrate All-Source Intelligence
Seamlessly integrate with your existing cybersecurity ecosystem to build a comprehensive intelligence infrastructure tailored to your specific needs. There are with many ways to consume and utilize threat intelligence, including:
- Industry-leading Mandiant Threat Intelligence
- SentinelLABS threat research
- WatchTower reporting
- Curated integrations in Singularity Marketplace
- Bring your own intelligence via API

Act on Insights with Managed Threat Hunting
Call on SentinelOne WatchTower Pro, which gives you a dedicated threat hunter to search every corner of your unique enterprise for unwanted risk—current and historical, external and internal.

